Overview
Cybersecurity research agencies around the world are warning organizations using VMware ESXi servers to patch an almost two (2) year old vulnerability to prevent being compromised by threat actors in the "ESXiArgs" ransomware campaign. Researchers conducted internet-wide telemetry across more than seventy (70) services and protocols, identifying 18,581[1] vulnerable internet-facing VMware ESXi servers. Thousands of organizations across the United States and Europe have already been compromised since the campaign started.
VMware ESXi is a Virtual Machine Monitor (VMM) that installs directly onto a physical server, allowing access and control of the underlying resources. As VMware’s hypervisor, EXSi enables organizations to run several virtual machines on one host computer and share memory, processing, and other resources. The years-old vulnerability is tracked as CVE-2021-21974 and is a heap-based buffer overflow flaw in the ESXi OpenSLP service. ESXiArgs threat actors who gain access to the network segment of a vulnerable ESXi server facilitate their attack by exploiting this flaw to conduct remote code execution (RCE).
The campaign has been dubbed ESXiArgs due to the ransomware creating an additional file with the extension ".args" after encrypting a document, which contains the ransom note with instructions for how to decrypt the encrypted files.
Ransomware Campaign
On January 31, 2023, an analysis of the ransom notes performed by the attack surface management firm Censys indicated that their platform’s telemetry had picked up artifacts of ransomware deployment on port 443 of two (2) different OVH-hosted systems. Digging deeper, researchers were able to identify that the ransom notes were also present back in mid-October of 2022. The ransom notes from October 2022 and January 2023 were compared, and researchers observed that while the notes were very similar, they did include a few distinct differences which are highlighted in the table below.
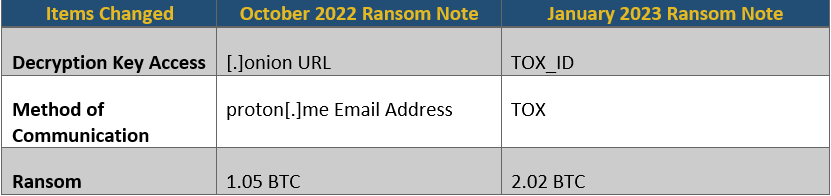
These changes likely indicate that the threat actors were testing the feasibility of their campaign tactics techniques and procedures (TTPs) for months before initiating the onslaught associated with the February 2023 wave of attacks.
In the first iteration of the ESXiArgs campaign, the ransomware encryption scheme worked by checking the file size. If the file size was less than 128 MB, the entire file was encrypted in one (1) MB increments. If the file was greater than 128 MB, the encryptor script would calculate a "size_step," alternating between encrypting one (1) MB of data and skipping the calculated size_step. For example, if a file was 4.5 GB in size, then the size_step would be forty-five (45), meaning that for every 1 MB of encrypted data, the script would skip 45 MB of the file[2]. This size_step feature allowed the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) to create a ransomware decryptor script[3] by leveraging the large amount of unencrypted data in files encrypted by the ransomware. The decryptor script enabled victims to bring compromised servers back online while data was restored from backups in the background. Unfortunately, this led the actors behind the ESXiArgs campaign to quickly modify the encryption script to encrypt 50% of all files over 128 MB, making them virtually unrecoverable without a key and rendering the CISA decryptor useless for newly-infected machines.
In early-to-mid-February 2023, a second surge in ESXiArgs attacks emerged after leveraging the newly modified ransomware strain. Researchers from Censys published a report on their blog indicating that they had already observed more than 500 newly infected hosts over just a few days[4]. The majority of the second-wave compromises impacted organizations in France, Germany, Ukraine, the Netherlands, and the United Kingdom. To make matters worse, researchers have identified a relatively new ransomware strain known as "RansomExx2" that has been observed targeting Linux machines and exploiting vulnerable ESXi servers. At this time, it is unknown if the RansomExx2 attacks are being conducted by the same threat actors as the ESXiArgs campaign.
Recommendations
To mitigate the risk of exploitation, CTIX analysts recommend that VMware ESXi administrators take the following four (4) steps:
-
Immediately update their VMware infrastructure to the most recent version for their deployment.
-
Remove any public-facing VMWare servers unless the service absolutely needs to be accessible via the internet.
-
Ensure that there is a backup solution in place in the event of an ESXiArgs compromise.
-
Regularly scan VMware infrastructure for vulnerabilities.
Attribution
This campaign has yet to be definitively attributed to a specific threat group[5], however, researchers have noted a few groups that could have facilitated this type of campaign. These groups include LockBit, the Royal Ransomware threat group, and the Babuk ransomware group.
LockBit is a potential contender due to their announcement of a new ESXi Ransomware variant in January 2023, however, none of the compromised data is available on their leak site. The Royal Ransomware threat group, which has quickly become the most prolific ransomware actor in recent months has expanded their operations to attack Linux platforms and EXSi servers, however, there are no concrete ties to EXSiArgs[6]. There are also indications that the Babuk ransomware group or their affiliates could be responsible, based on similarities with the leaked Babuk source code from 2022. Finally, there is the possibility that an unknown organization or existing threat group with undiscovered ties to ESXiArgs is responsible for the campaign.
CTIX Analysts will continue to monitor this matter as it develops in real time, and further publications may be released in the future.
Pierre Jeppsson, Senior Associate at Ankrua Consulting Group, authored this article.
References:
[3] https://www.recordedfuture.com/esxiargs-ransomware-targets-vmware-esxi-openslp-servers



 />i
/>i

